A distributed denial-of-service attack (DDoS attack) is an attempt by a hostile individual or group to make a machine, or a network of machines , unavailable to its users. Motives and the means to carry out such attacks can vary from one case to another. However, the general intention is to temporarily or indefinitely cease the services of the host that is connected to the internet.
Usually, DDoS attacks are launched against services that are hosted on large web servers, like bank sites, credit card payment gateways and root name servers. Whatever the motive may be, the fact remains that your business needs to be fully protected against DDoS attacks.
How DDoS Attacks Work
Typically, attackers use non-trivial amounts of computing resources to send bogus traffic to a website. If enough of this bogus traffic is directed at said website, legitimate users (i.e. your customers) will not be able to use the services on your website.
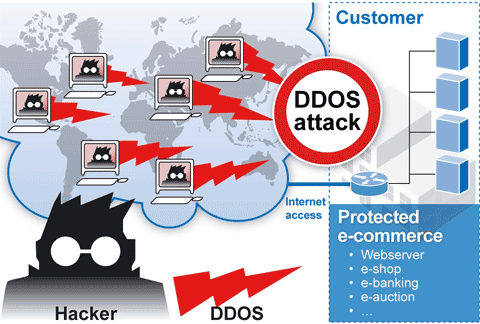
For example, consider a DDoS attack on an online banking site. If the website can handle up to twenty people a second attempting to log in to their accounts, the DDoS attacker will send twenty fake requests second, making legitimate users unable to log in. The website will either be too slow to respond adequately, or will be unable to respond at all.
Methods of DDoS Protection
- DIY Protection: This is simple, but isn’t too effective against sophisticated attacks. The idea is that Python scripts are written to filter out bad traffic, or the company sets up firewalls to block the bad traffic instead. This is unfortunately too weak to defend against larger attacks.
- On-premises Equipment: This is when a company will invest in dedicated DDoS mitigation appliances. This involves housing specialised hardware in your data centre, along with your servers, so they are able to filter out bad traffic. This can be problematic, though, because of the costs of maintaining them and the time consumed in updating them against the latest threats.
- ISP Protection: Internet Service Providers can also supply your enterprise with DDoS Mitigation, as they will have far more bandwidth than your enterprise would, a crucial advantage when it comes to dealing with volumetric attacks. Unfortunately, this type of protection comes with its own problems too. As ISPs are primarily concerned with selling bandwidth, they won’t necessarily invest in the required resources to stay on top of the latest kinds of DDoS threats. This method also lacks cloud protection.
What’s the Best Method?
Given the speed and efficiency at which new DDoS attacks are designed and deployed, it’s necessary for your company to have the most robust and flexible type of protection possible. In today’s environment of increasingly complex and debilitating cyber threats, it’s essential that you have the best of the best protecting you.
Fortunately, this is a service that is provided by cyber security firms like NCC Group. They can offer round-the-clock protection off-site, so that you won’t have to be concerned about overloading your data centre and IT staff with maintaining protection and constantly updating against the latest threats.
They will also have massive amounts of network bandwidth to accommodate for any size of network traffic, filtering out the clean traffic to send to your data centre. With a security firm handling these concerns for you, you’ll be guaranteed expertise as well as several different types of DDoS mitigation hardware. You already know how damaging cyber attacks can be for your business: if you want to survive, it’s best to go with the best. To read more story, Please visit our blog.