Security threats are common in large organizations, whether it is an external attack like distributed denial of service (DDoS) or a malicious activity initiated by a user in your organization. DDoS is a denial of service (DOS) attack where a Trojan affects multiple systems but targets a single system resulting in a security threat. Internet hackers get into your system and steal sensitive data and intellectual property from your organization through user credentials. These cyber ‘thieves’ employ a number of tactics such as a password brute force, phishing links, keyloggers, and password scanning to put your enterprise network at risk. This is the reason why you need privileged access management (PAM) to prevent data theft. Read on to learn how PAM works and what its numerous benefits are.
How Does PAM Work?
A PAM solution helps your business to manage small groups of privileged accounts instead of creating and maintaining multiple user-specific accounts. When an authorized person requests access to a privileged account, he opens the application interface and asks for the account type required, for what reason, and for which time period. When the person gets an access depends on the company’s rules, policies, and the requester’s traits. In other words, the user may get immediate access, may have to wait for the System Owner’s approval through dual control, or may have to wait for some time.
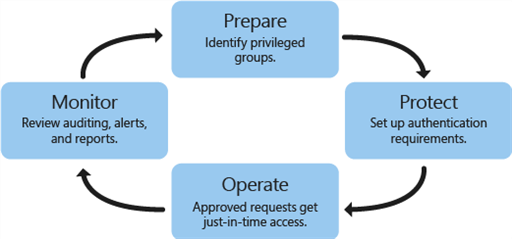
You may get automated or fire-call approval in an emergency situation at night when no authorized approver is available at the office. Pre-allocated individuals can automatically gain access for a limited period. A request to access can also be auto rejected if not accepted within a particular time span. In such a scenario, a request can be auto-escalated to the next approver. The system owner exercises complete control and has the authority to refuse access to accounts, if necessary. Administrators can ensure that user account passwords are modified every few minutes or hours to ensure a high level of security and control. All events are audited whether they are initiated at a connected system, server, or an end-user interface. This means all actions performed by approvers and requesters must include remarks as to why accounts were used and why approvers took certain actions. This way, auditors get a fair idea of compliance.
PAM makes the auditing process simpler. System owners and end users get auto email notifications concerning specific accounts whose access were surrendered, approved, rejected, automatically expired, or are about to expire.
Benefits of PAM
PAM reduces or eradicates the risks associated with security threats, data thefts, privacy breaches, frauds, and compliance violations due to shared accounts in your enterprise. Here are some of the benefits of privileged access management:
Prevents careless use of privileged accounts: All account access depends on the approval and review from authorized staff, system owners, and managers. This discourages the use of privileged accounts for routine operations.
Tracks usage of a particular user: PAM tracks, controls, and manages privileges across several shared accounts in an enterprise. This means that you can track usage back to any particular user in your organization.
Simplifies and expedites your audits: Essential business data is securely stored in the database and is easily integrated into your company’s compliance reports.
Prevents unauthorized access: PAM blocks unauthorized access to the highly privileged and shared accounts. Frequent password changes ensure complete security of all the accounts across the organization.
Auto-documentation of the compliance process: PAM helps you know who is authorized to execute an administrative task, who is an approver, the reason behind account usage, and the complete account histories. This, in a way, increases accountability and adds clarity to the whole process.
Privileged access management secures your business data against cyber hackers. It provides a simple solution to ensure that only an authorized user have access to your company’s intellectual property. This is important to prevent your company’s mission-critical systems against security breaches.